The 3 pillars of an effective cybersecurity program
Overcome the obstacles of network security in the age of IT-OT convergence
Fight cyberattacks and their impacts with a strong response plan
In a recent Fluke Accelix Best Practice Webinar, “Managing cybersecurity risk in maintenance and reliability,” more than 100 manufacturing professionals were asked to rate the importance of cybersecurity when considering maintenance and reliability software solutions. Their four choices were: mission-critical, somewhat important, not important, and not sure.
None of the attendees answered, “not important” or “not sure,” indicating that the risk of a cyberattack can no longer be ignored. The answers were as follows:
- Mission critical - 68%
- Somewhat important - 32%
- Not Important - 0%
- Not sure - 0%
Cyberattacks on manufacturing and other industries
Barely a day goes by without a new report of ransomware attacks on a big company.
Cybercriminals consider manufacturing a high-value target. According to a June 2021 research report from Morphisec, manufacturing accounts for nearly a quarter of ransomware attacks. The study also found that 1-in-5 manufacturing companies in the U.S. and U.K. have been victims of cyberattacks over the last 12 months alone.
Phishing, data theft, supply chain, and ransomware attacks have come to be expected. Malicious actors steal credentials, expose sensitive data, and hold intellectual property ransom. Some attacks affect organizations so viciously that they are forced to pause or halt operations, losing millions of dollars in downtime and time spent recovering from the event.
A prime example involved JBS USA Holdings Inc., one of the world’s largest meat processors, which was hacked on May 30, 2021, forcing the company to shut down its North American and Australian plants. JBS acknowledged paying the Russian criminal group REvil an $11 million ransom to prevent further disruption.
A month earlier, this same hacker gang stole confidential files from Apple partner, Quanta Computer Inc., the largest laptop manufacturer in the world. The hackers tried to extort $50 million from the multinational technology company in exchange for not leaking schematics and images detailing the plans for an upcoming laptop release. It is unclear whether the ransom was paid.
Defend cyberattacks in manufacturing using preventive maintenance
Scheduling preventive maintenance (PM) tasks to help keep equipment operating is essential. But it is not the only kind of maintenance you should plan. Performing PMs regularly on your SCADA, PLC, Computerized Maintenance Management System (CMMS), and others will reduce cybersecurity vulnerability.
By scheduling downtime to update software and apply patches, you keep your cybersecurity environment hardened. Hardening is a form of cyberattack protection that requires closing system gaps that hackers often use to seize the system and gain access to sensitive data.
It is also critical to know what you will do if you experience a breach. Take the time to develop and prepare response protocols and disaster recovery plans when an attack occurs.
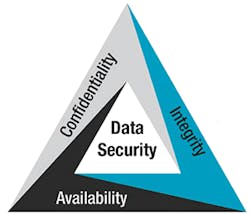
Adopting the data security CIA triad
Confidentiality, integrity, and availability are the three most commonly recognized components of cybersecurity. Known more customarily as the CIA triad, organizations often use this model to build a cybersecurity foundation. Generally, if one or more of the triad components is violated, the risk of an attack increases.
Frederic Baudart is lead SME manager for Fluke Corp., focusing on the company’s reliability and condition monitoring product lines. Baudart holds technical degrees in electrical and instrumentation engineering from Chome-Wynz technical college. Mathew Hudon has 15 years of experience in designing and implementing secure IT solutions. He has been leading cybersecurity for Fluke Reliability for the past two years.
Establishing information security policies based on the CIA triad directs a team to make essential decisions about which components apply most to specific data sets, such as sensor data and the entire organization.
3 tips for deploying the cybersecurity triad in maintenance
1. Confidentiality
Objective: Ensure that private information stays private and can only be accessed by vetted individuals.
Only core personnel should have permission to access data. To reduce the possibility of a breach, limit entry points to sensitive data to as few people as possible. Scrutinize who has access and grant permission based on what they need to do their job.
What can you do right now? Examine your organization’s data access levels, including corporate secrets or info that permits control over sensitive equipment, such as a SCADA system. Many organizations categorize the importance of data to help identify how much damage it would cause if released.
2. Integrity
Objective: Ensure the data is trustworthy and accurate and has not been inappropriately altered.
Data integrity refers to the validity and accuracy of the data throughout its lifecycle. Data in a CMMS or SCADA system must be accurate. The company’s operations department and its ability to demonstrate regulatory compliance depends on reliable data.
Inaccurate data can damage a relationship with a customer, but it can also cost a company a lot of money. According to a 2013 Gartner study, organizations surveyed estimated that inaccurate data costs them on average $14.2 million annually. If you cannot show auditors how and why your regulatory compliance documentation evidence is accurate, they could penalize your organization.
What can you do right now? Evaluate the level of data accuracy in your primary systems and perform an audit if you do not fully trust the data. Decide the level of confidence you require in your maintenance records and identify vulnerable points and if they need protection. Adopt controls that prevent unauthorized users from making erroneous changes or deleting data accidently.
3. Availability
Objective: Ensure that data is available to be used when it is needed to make decisions.
Maintenance data must be available on-demand. You should know the uptime percentage that enables an enterprise asset management (EAM) system and other critical systems to supply what is necessary continuously. Maintenance systems must be protected from corruption to allow the systems to serve the organization.
What can you do right now? Commit preventive maintenance (PM) best practices to the IT infrastructure supporting your processes. Ensure you understand what is necessary to maintain availability and schedule downtime to run patches that harden the system to reduce external entry points.
Key takeaways
- The right people and controls must be in place to protect your data’s confidentiality, integrity, and availability.
- Operations and maintenance must understand the sensitivity of the data under their care.
- Operations, maintenance, and IT must work together closely.
- The human element is one of the biggest reasons data gets breached. Educate your workforce to decrease accidental breaches.
- It is crucial to partner with your IT and security departments. By involving them early, they’ll be able to help you mitigate cybersecurity issues more effectively.
- Develop a high-level IIoT and cybersecurity checklist that includes equipment, communications and protocols, environment, and security.
This story originally appeared in the October 2021 issue of Plant Services. Subscribe to Plant Services here.
This article is part of our monthly Tactics and Practices column. Read more Tactics and Practices.