The threats to industrial control systems are real and alarming. Building an effective defense is something few companies can or should undertake singlehandedly.
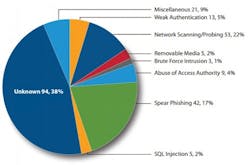
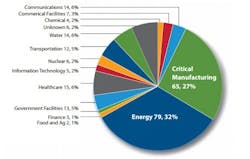
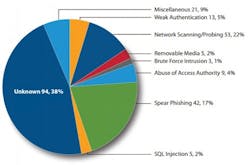
In a report released in March, the US DHS ICS-CERT (Industrial Control System Computer Emergency Response Team) cited 245 documented cyber attacks on industrial control systems in the period between Oct. 1, 2013, and Sept. 30, 2014. Keep in mind that those were attacks that were recognized and reported. One can assume that there were far more that were not detected and others where the victims did not feel inclined to make the incident public.
While this statistic can be analyzed and interpreted many ways, one thing is clear: Industrial networks and control systems are under attack. To the management of a manufacturing company looking at this reality, how should responsible leaders act?
One approach is simply to do nothing: business as usual and hope for the best. Some companies assume implementing a firewall is enough defense considering the odds of an attack. With luck that might work, but it is similar to leaving the doors unlocked with hope that the wrong person won’t try to get in. Still, if a company can operate easily without automation and there is little in the way of information to steal, the risk can be very low. Why buy locks for a building if there is nothing in the building of any value?
For a company of any substance, this is not practical. The risk is simply too great.
A more comprehensive approach
A more-effective solution program for the long term has to begin with a careful analysis of where a company is in the larger picture. What is the company trying to protect? What is its overall security concept, and how does it fit into the larger organizational concept? To put it in more practical terms:
- What risks do you face? Do you have any concept of who might want to attack your systems and how? Have you already experienced cyber attacks?
- What information or data might someone want to steal?
- How could an attacker disrupt your production?
- Is there potential for an environmental disaster or loss-of-life scenario?
- Should people in communities surrounding your facilities be concerned?
- How could any of those possibilities affect your relationships with customers and stakeholders?
Building a cyber defensive program that is truly comprehensive is very difficult to do internally. It is a process, not an event. There are technical elements, but it must involve your employees with training on secure work practices and behavior.
Working with an industrial cybersecurity expert to develop defensive strategies and manage them over the long term can overcome many of the drawbacks of trying to take that challenge on single-handedly or ignoring the risk. This expert brings the collective experience of working with a wide variety of companies, promotes best practice and provides valuable expertise to assist customers in understanding their current cyber security capabilities. Many companies are hobbled because they "don’t know what they don’t know," but drawing on experience from outside can fill in those gaps.
Siemens uses the following three-step process to build industrial cybersecurity programs for its customers:
- Assess: Analyze your present security environment and develop a security roadmap. This is always an eye-opening experience as companies typically do not have a comprehensive grasp of the nature of their industrial networks or what data could be compromised.
- Implement: Engineer, design, and implement a cybersecurity program based on your specific situation to protect the gaps between your level of protection and potential risk, creating a program that follows important industrial security standards such as ISA 99, IEC62443, NERC-CIP, and others. Siemens applies standards, best practices, and security frameworks resulting in a Defense-in-Depth approach which includes the use of Secure Automation Cells.
- Operate and Manage: Continuous detection and protection through proactive defense. Support is provided for maintaining your security posture against current and potential cyber threats. Your adversaries are intelligent, and they are always looking for new ways to get into your system.
An ongoing process
Ken Keiser is Practice Lead, Plant Security, for Siemens Industry, Inc. Ken has spent more than 30 years in the process control industries with Fischer & Porter, Bailey Controls, ABB, and Siemens. In the last five years, he has also concentrated in Industrial Cyber Security within the Siemens Process Automation segment. He has worked with ISA99 on various workgroups, is the Industrial Security liaison to key Siemens customers, and recently received his CISSP certification from (ISC)2. Ken has an Electrical Engineering degree from Drexel University and a Business Administration degree from Temple University.
Ongoing services for managing and maintaining your security against current and potential cyber threats are a critical element. A cybersecurity operations center such as the Siemens CSOC can provide 24/7 monitoring as well as operations and updates of deployed security controls based on real-time intelligence. Proactive monitoring and continuous security management reduces the risk of production loss and equipment damage caused by cybersecurity threats and protects intellectual property, company reputation, and brand image.
In addition, on-demand remote-incident-handling support should be implemented, ideally with ICS cybersecurity experts available to respond quickly to support you in executing forensic investigations, containing possible damages to your environment, and eradicating risks.
When industrial manufacturing leaders partner with effective cybersecurity services providers, they allow their internal resources to concentrate on the core business. They also provide protection for their company’s assets, people, and customers.
Reference:
1. National Cybersecurity and Communications Integration Center (NCCIC), 2015. "ICS-CERT Monitor, September 2014-February 2015."