Is your CMMS system really secure?
Like any revolution, the information age ushered in the really good along with the really bad. Information systems can be a phenomenal management tool when used as intended, or a tool for wreaking havoc on a department or entire company when controlled in the wrong manner. The concept of "security" prevents the latter scenario from playing itself out, whether by accident or deliberately.
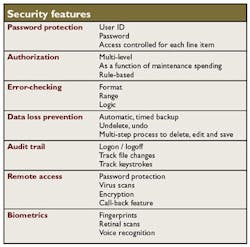
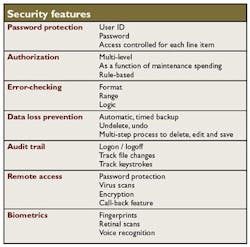
When people refer to software security, they typically are thinking of password protection for logging onto a given software package. This is, however, only one of many features that constitute the security of a computerized maintenance management system (CMMS). In general, security can be defined as protecting the system from unauthorized or accidental deletion, addition, editing, access or even viewing of data. CMMS vendors and their partners use many features to ensure a secure environment.
Password protection is the most basic form of security that blocks unauthorized access to the CMMS upon logon. Thus, users trying to get into the CMMS will be confronted with a request for a password, which must be validated before the package opens for use. Some systems require a user ID and a password. However, this isn't necessary if each user has a unique password. The better systems force the user to enter a minimum number of case-sensitive password characters. Attempts at entering a password can be limited (usually to three), and users can be forced to change their password on a predefined cycle (e.g., every three months). This makes it harder for hackers to crack the code.
Some systems also demand a password if the user hasn't been active during a specified timeframe. This control is similar to password-protected screen savers, which the operating system invokes regardless of the application being run.
More sophisticated CMMS packages offer access control for each menu line item, function key and screen. User access options include complete access denial, read-only rights or read and write privileges. If users try to access a menu item, function key or screen for which they have no rights, the CMMS blocks entry. In some cases, the CMMS provides the option to either "grey out" the menu items or functions classified as "denied access," or not show them at all. Thus, menus and screens can be custom-tailored.
The most sophisticated security systems restrict access down to the field level. Although a user may have read/write access to a given screen within a menu item, access to a given field may be denied or read-only. Here, too, unauthorized fields can be greyed out or completely hidden from view to avoid temptation, clutter and confusion.
Security access can be defined for each individual user and user group. Groupings such as supervisors, maintenance planners and so on can be defined and given equal access rights within a given group. This helps to simplify the setup and avoids treating users inequitably.
Authorization is another form of security that is the electronic equivalent of an authorizing signature. Work orders, purchase orders and other documents typically require approval by a supervisor before processing can proceed. Some systems allow multi-level approvals; for example, various dollar ranges will require multiple signatures. One useful feature to look for in a CMMS is the ability to require another signature automatically if actual expenditures begin to exceed the original estimate by a user-defined percentage. This prevents planners from low-balling estimated expenditures to avoid higher-level authorization.
One of the most comprehensive systems customizes authorization schemes by allowing users to establish limit rules on the basis of work groups and type of approval. For example, the system can request the next level of authorization when the actual dollar expenditure logged exceeds a user-defined percentage. Thus, work orders or projects can be monitored for significant overruns. The system also could be set up to allow only certain people to approve emergency work orders. A user-definable workflow with configurable approvals is a feature that allows users to establish password protection on configurable status changes for work orders, parts, purchase orders, employees and so on.
Error-checking can be a means of catching honest mistakes or deliberate attempts at breaching security. The three types of error checking are based on format, range and logic. Checking for format ensures that, for example, part numbers begin with two alpha characters followed by five numerals. A check on range could prevent, for example, an attempt at entering a vendor number that isn't between 15000 and 35000. Error checking for logic verifies that a given value makes sense: the right engine is assigned to a given vehicle or the right number of pumps for a given "parent" piece of equipment. Some CMMS applications allow users to define an entire formula or program to determine the validity of data entered into a given field.
Data loss prevention is another security feature. There are few things more frustrating than being surprised by evaporating data, especially after many hours of tedious keystroke entry. Software programmers have many ways to secure the data and prevent accidental loss or deliberate data destruction. The most common is to assist users in properly backing up the data through an automatic or timed backup. Often this is established outside the CMMS.
"Undelete" and "undo" are common features that allow users to bring back deleted text and reverse unwanted keystrokes respectively. The simplest feature for preventing data loss is prompting the user with "Are you sure?" before the software deletes, edits or saves data.
Audit trails provide a separate file that tracks the logon/logoff activity. More sophisticated audit trails list data file changes by user, date and time. The most detailed audit trail can log the keystrokes by each user, a feature that quickly gobbles disk space and could even slow down system response somewhat. Audit trails are sometimes features of the operating system or third-party software.
Remote access represents one of the more sticky security issues facing corporations. As mass storage devices, such as DVDs, CDs, tapes, removable hard drives and memory sticks, become cheaper, smaller and carry more information, companies have become almost paranoid about data loss, spreading viruses and corporate information falling into the wrong hands. Some relatively small storage devices are capable of holding the equivalent of a warehouse of paper files. Few companies have procedures for ensuring data security on these devices.
Three important software solutions for protecting the data are password protection, virus protection and encryption.
Another possible security breach is through remote access to an office computer via a home computer, notebook computer or personal digital assistant. One technique that avoids problems with dial-up access is a dial-back feature. The host computer hangs up with the remote computer and dials back a pre-designated phone number that corresponds to the initial logon ID and password. For additional Internet security, some companies use sophisticated key fobs that require a match between host and the ever-changing key. A less complex method of security includes one or more levels of password protection, but this can more easily be broken by hackers.
Biometric security is one of the fastest growing means of authentication for remote or local access. This includes identification by means of fingerprints, retina scans, voice recognition and the like. Is this "Big Brother" or peace of mind? The debate continues...
Contributing Editor David Berger can be reached at [email protected].